Open Sausa
When rumors were floating around that SUNW^WJAVA was about to open source Java, there were those who didn't believe it, those who would believe it when they see it, and those who believed it's just a matter of time. I've always been in the third camp, and it turned out that I was right.
Similar rumors floated around for a long time, that AMD/ATI was going to open source their graphics card drivers. I knew it would happen, and it's just a matter of time. So when AMD/ATI announced they are going to open up the spec to their radeon line of hardware, and have a 2D open source driver out by year end, I immediately purchased the best radeon card that has stable open source driver, the radeon 9250.
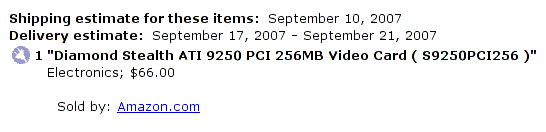
Just to put my money where my mouth is.
Logitech Access Keyboard and function lock

I've had this keyboard ever since my previous one failed (due to a combination of orange juice and some not-so-pure H2O), I am generally happy with it, except this:

The function lock, when off, turns all the function keys into special purpose keys that I never use. Worse yet, the lock is off by default and there is no way to make it stay on across power cycle. So for the past 2 years I've been manually (since there's no way to toggle the function lock programmably) switching the lock on, still I usually begin my day hitting my function keys couple times and wonder why they don't do what they are supposed to do.
Today I finally decided to figure out a way to stop this madness. Turns out you can fool Linux into thinking that those special purpose keys are the same as the function keys. See Solution for F-lock. I had to modify the setkeycodes line for my keyboard to:
setkeycodes e03b 59 e03c 60 e03d 61 e03e 62 e010 63 e019 64 e022 65 e024 66 e043 67 e044 68 e057 87 e058 88
Otherwise F5-F8 wouldn't work. Now I will be able to save 2 seconds every day for the next 2 years! (My previous keyboard lasted about 4 years)
Anti-comment spam update
Looks like key rotation isn't working as expected:
67.15.18.27 - - [19/May/2007:09:25:36 -0700] "GET /post.ml?reply_of=56 HTTP/1.1" 200 7586 "-" "Mozilla/4.0 (compatible; MSIE 5.0; Windows 98; DigExt\\)"
67.15.18.27 - - [19/May/2007:09:25:37 -0700] "POST /cgi-bin/post.pl HTTP/1.1" 200 5190 "http://hxbc.us/post.ml?reply_of=56" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)"
67.15.18.27 - - [19/May/2007:09:25:57 -0700] "POST /cgi-bin/post.pl HTTP/1.1" 302 5 "http://hxbc.us/post.ml?reply_of=56" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)"
67.15.18.27 - - [19/May/2007:13:20:42 -0700] "POST /cgi-bin/post.pl HTTP/1.1" 302 5 "http://hxbc.us/post.ml?reply_of=56" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)"
The 5 seconds delay clearly worked the first time, and the spammer proceeded to repost the comment 20 seconds later. I wonder how he is able to post again nearly 4 hours later, without getting another secret token.
I have another plan to make the spammers' lives more difficult, which I will probably implement this weekend.
A Plan Against Comment Spam
Those of you who are silly enough to check this space everyday should have noticed that this site has been plagued by comment spam recently. In the last couple days I have deleted more than 100 spammy comments. Tonight I've decided that I've spent enough time deleting them (2 for loops in bash, really), so I sat down and implemented some anti-spam logic that I've thought about in the past few days.
Looking at the server log I noticed each of the spam comment involved a single POST to the comment CGI script only. The spam bots don't GET the comment page, and each IP posts only one comment. The content varies, but it's usually about Viagra. I can probably just filter out comments using keywords, but some comments contained only links and nothing else. I also don't want to do CAPTCHA or other things that depend on the spammer not being smart enough.
Now each time you request the comment page, you are given a base64 encoded secret. The secret is your IP and the current timestamp encrypted using Blowfish. When the comment is posted, I decrypt the secret and check that the poster's IP is indeed the same IP I handed the secret to. I also check that it's been at least 5 seconds since I handed out the secret, to avoid bots GET'ing the page and then POST'ing immediately. Finally, the secret is only valid for 1-2 hours. This is implemented by prepending the current hour to a secret to construct the key, and fallback to the previous hour to handle the borderline case. This is probably more difficult than it's worth since I can simply check the timestamp that's in the secret, but I figure that rotating to a different key every hour is probably not a bad idea.
Implementing it took more time than it should because the Crypt::CBC module on dreamhost is older than what I have on my local machine. I ended up copying the local copy to the server and use that instead.
This is all I am going to do for now. I realize that it's not perfect (for example, a bot can get the secret and keep posting from the same IP for 2 hours), but hopefully is enough to deter most spammers.
Pidgin
Gaim, everyone's favorite IM client, has been renamed to Pidgin. The name change has been planned for a long time, but was formally announced today. I found out about this on April Fool's day, you can probably imagine my disbelieve at the time.
Gaim is dead, long live Pidgin.
It has a new look as well:

Props to Hylke Bons for creating a new set of Gaim^WPidgin icons.



